 "Terrorism has joined the ranks of
a foreseeable risk." This statement appeared in the Nov/Dec issue of Executive Legal Advisor
Magazine. It has legal ramifications. It means that
organizations will be held to a higher standard of care. That means
that entities that fail to prepare for a terrorist attack could be held
liable for their negligence in the legal system. Planning, education
and compliance are three key areas that can help protect executives and
organizations from having suits brought against them in the event of a
terrorist attack. In Part I
of this series I covered physical security, building design and
business continuity planning. Part II will address corporate
counter-terrorism compliance.
"Terrorism has joined the ranks of
a foreseeable risk." This statement appeared in the Nov/Dec issue of Executive Legal Advisor
Magazine. It has legal ramifications. It means that
organizations will be held to a higher standard of care. That means
that entities that fail to prepare for a terrorist attack could be held
liable for their negligence in the legal system. Planning, education
and compliance are three key areas that can help protect executives and
organizations from having suits brought against them in the event of a
terrorist attack. In Part I
of this series I covered physical security, building design and
business continuity planning. Part II will address corporate
counter-terrorism compliance. This article looks at several pieces of legislation and other compliance programs that were put into effect after the terrorist attacks of September 11, 2001. In each case, I will give a brief overview of the act and a description of "experiments" that I conducted to see how well the new regulations were being followed. To make a long story short, the answer to how well regulations are being followed is, "not well at all."
Counter-terrorism Compliance
The most notable of piece of legislation is the U.S. Patriot Act, which has become a lightning rod for controversy. Best known for the expansion of surveillance that includes electronic monitoring as well as access to library records, the act really encompasses much more.
Ten Titles of the U.S. Patriot Act
- Enhancing Domestic Security Against Terrorism
- Enhanced Surveillance Procedures
- International Money Laundering Abatement & Anti-Terrorist Financing Act of 2001
- Protecting the Border
- Removing Obstacles to Investigating Terrorism
- Providing for Victims of Terrorism, Public Safety Officers and Their Families
- Increased Information-Sharing for Critical Infrastructure Protection
- Strengthening the Criminal Laws Against Terrorism
- Improved Intelligence
- Miscellaneous
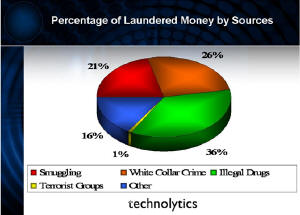
Early on, it became evident that a significant impact on fighting terrorism could be made if the government could cut off funding for these activities. The government chose to enhance existing legislation designed to combat drug trafficking, smuggling and organized crime to extend its effect to the financing of terrorism. Currently, international money laundering estimates range between $590 billion to $1.5 trillion dollars annually. As the graph below shows, only a very small percentage is likely being used to finance terrorists.
 |
Investigation - In one instance, I was able to conduct transactions (purchasing multiple money orders) without providing any kind of identification. I sent an email to the business ethics hotline for the company and received a reply I could not believe. They said that they recently became aware of the fact they were not in compliance and retained outside legal representation to assist them. I replied by asking them, if they knew they were not compliant, then why did they continue to break the law and sell money orders? I never received a reply.
In another instance I researched check cashing operations and their requirements to comply as MSBs. I found one check cashing franchise operation with over two dozen franchise locations. I called and spoke with a manager in their operations who assured me they were in complete compliance. All MSBs are required as a part of compliance to register their operations. None of the over two dozen locations had registered.
Perhaps the most troubling finding in my investigation came from my discussion with a member of the Board of Directors of a moderately-sized bank. In our conversation, he stated that he was not very concerned about making sure the bank was compliant – they were small and the Federal Regulators would not be worried about them. It is this attitude that places all of us at greater risk.
Technology - Money laundering and tracking terrorist financing requires the development of social networks. A social network is a graphic representation and map of the relationships between individuals or organizations. This tool indicates the ways in which they connect through financial transactions that often occur in multiple locations around the world. GIS and LIS are key technologies that combine to create this graphic map, which allows the illicit funds to be traced by authorities. Currently many of our nation’s largest financial institutions have sophisticated systems in place that assist them in complying with anti-money laundering regulations.
Bio-Terrorism Act
 Another
important piece of legislation is the Bioterrorism Act. This
act is designed to help protect against, detect and track an attack on
the food supply. It requires organizations that are involved in
processing, packaging, production, transportation or storage of food to
be able to track where the product(s) came from, where they were
stored, who had access to them and to whom they were sold or delivered.
In addition, all food handling facilities, with very few exceptions,
must register (much like the MSBs) under the anti-money laundering act.
Organizations of 500 or more employees are required to have the
tracking capabilities in place now. Organizations between 11 and 499
employees have until June 2006 and organizations under 10 employees
have until December 2006 to comply.
Another
important piece of legislation is the Bioterrorism Act. This
act is designed to help protect against, detect and track an attack on
the food supply. It requires organizations that are involved in
processing, packaging, production, transportation or storage of food to
be able to track where the product(s) came from, where they were
stored, who had access to them and to whom they were sold or delivered.
In addition, all food handling facilities, with very few exceptions,
must register (much like the MSBs) under the anti-money laundering act.
Organizations of 500 or more employees are required to have the
tracking capabilities in place now. Organizations between 11 and 499
employees have until June 2006 and organizations under 10 employees
have until December 2006 to comply. Investigation - I did not have to go very far to investigate compliance with this act. I was recently on a plane traveling to New York and was working on a PowerPoint presentation for a client on the company’s current state of compliance with the bio-terrorism act, when a woman sitting next to me reading over my shoulder interrupted me. She said she worked for a large organization in the food industry and asked me when this act was going into effect. When I told her, she said that there was no way her company could comply. She went on to explain that they rely heavily on vendor managed inventory and it would be a significant effort for them to make the changes necessary to comply with these requirements.
While I was in the wine country, I began inquiring if the operators of the winery had ever heard of the bio-terrorism act. Four out of seven had never heard of it, so the likelihood of the operations being registered or compliant is very small. In addition, the physical security and the layout of the facilities were not conducive to protecting the process or products from tampering.
Technology - A complete picture of the chain of custody of food products is needed in order to comply with the Bioterrorism Act. GIS and LIS combine with traditional ERP systems to present a complete picture of logistics, inventory and order information to make compliance with the Bioterrorism act much less painful. The ability to track vehicles that deliver food products enhances oversight by producers and companies purchasing food supplies. For additional details please refer to the Bioterrorism and the Food Supply article published Oct 01, 2004 in Directions Magazine.
Customs & Trade Partnership Against Terrorism (C-TPAT)
The U.S. Government, in an effort to protect our ports of entry and commerce, formed a partnership with the trade community to assist in the war against terrorism. The Customs Trade Partnership Against Terrorism, or C-TPAT, is a voluntary compliance program. The intent is to use companies involved in international commerce to assess the security and vulnerabilities within their supply chains and complete specified documentation. After submitting the proper documentation and receipt of final approval, a company becomes certified as C-TPAT compliant. The carrot for compliance is an accelerated handling of goods moving through the border. Many large organizations are beginning to require critical suppliers to obtain C-TPAT certification in an effort to guarantee the supply of critical goods.
Investigation - I asked a variety of departments within seven companies about their C-TPAT status. Surprisingly, eight out of 10 respondents already had documentation submitted and were awaiting certification. One organization had already received C-TPAT certification and was waiting for Customs to enact the rest of the program.
Technology - Just like compliance with the Bioterrorism Act, C-TPAT certification is made much easier with GIS/LIS integrated with the data for the ERP systems and connected to the EDI advanced shipping notifications from trading partners around the world. The combination of these capabilities provides the foundation needed to securely conduct international commerce.
Education
Education is an important part of protecting our nation against terrorist attacks. While education is a requirement for compliance with the anti-money laundering regulations, it does not address several other key areas in the multi-layer security blanket that protects us. One issue that has may professionals concerned is the training of private security forces and providers of security guard services. There are many high risk soft targets across the nation that are protected by these private security forces. There are multiple state regulations that specify training requirements for security guards. Overall, the training requirements range from none to 40 hours, while corporations using their own employees as guards may define their own training requirements.
Investigation - In Part I of this series, there was a photo of an entrance to a mall which was a possible target of a terrorist plot that was foiled by the FBI. One year after the news release about the foiled plot, I went to the two malls that were named as possible targets. I talked to several security guards about what counter-terrorism training they had received. All referred me to the chief of security. When I called the chief of security, he referred me to the mall’s public relations firm, which in turn, offered me the year-old press release.
I did finally find one guard at the mall who would talk about the training he received. He said he was one of the most highly trained guards. He received about 30 hours of training, most of which was firearms training ‑ he received no counter-terrorism training. I could not confirm that any security guards had received any training with regard to terrorism. One employee said, "At this point, I am relying on luck."
I pushed further on this education issue and found a guard for a chemical plant who worked directly for the chemical company (not a private security company). He stated that in the last four years, he had received about 30 hours of training in emergency response and about six hours related to terrorism. Perhaps the most shocking conversation I had was with a police officer of a small municipality. He stated that, other than informal discussions, he had received no training on terrorism. When I asked him if he knew the most common remote detonation device for an improvised explosive, he replied that he had no idea. In discussions with several first responders, many of them stated that they had yet to receive training on the many aspects of terrorism.
Tracking terrorist financing, money laundering, food products, and products entering the country through our hundreds of ports requires high volume location-based systems. GIS, GPS, active RFIDs and Identity Management solutions, coupled with asset tracking and management capabilities, are the core components of the technology foundation for compliance. Several organizations have these systems in place, while the vast majority of businesses do not. In fact, it would be next to impossible to comply with many of these regulatory requirements without location-based information systems.
The government can regulate all it wants, but the benefits will be limited unless everyone complies with the requirements. The best way to improve security and safety against terrorism is the use of "carrots" as illustrated by the C-TPAT program. Even though some regulations have rewards for whistle blowers, not everyone is in compliance. This places all of us at risk! We need to ensure that all public and private security, law enforcement and first responders are properly trained and equipped to deal with the foreseeable threat of terrorism.