Information Technology and Homeland Security
Information technology has dramatically changed the way we secure our
nation. Few people would dispute the fact that in place of a massive
spy network, we have now sophisticated information-gathering systems.
For the most part the security of our nation rests in the silicon within
these systems and the people who analyze the massive amount of information
they collect 24 hours a day, seven days a week, 365 days a year.
From eavesdropping on cell phone conversations to listening in on satellite
communications to multifunction sensors, the intelligence we gather is
the fundamental protection against terrorism. For years now we have
read articles on the so called electronic listening stations and their
ability to intercept almost, if not all, types of electronic communications.
In the not so distant past we heard about carnivore, the FBI system that
would intercept emails on the internet. These current capabilities
will pale in comparison to the systems currently under consideration or
in some cases in development.
We have all seen the articles in the media about bits of information we have collected and used to foil terrorist plots. You may also recall we had the ability to listen in to Osama Bin Laden's satellite phone conversations. However, once it was reported via the mass media he stopped using his satellite phone. Imagine that! Another story that received far less media attention was the assassination of a foreign leader via a missile that honed in on his cell phone signal. The fact is that information technology has become integrated into almost every weapons system in today's modern military.
There are many applications of information technology in the fight to
defend against terrorism. Cyber attacking tools that might allow
one country to electronically transfer the funds out of a terrorist organization's
bank accounts or to place a web bug on their computer so every time they
send an email the intelligence agency would also receive a copy.
The applications of information technology to homeland security or to warfare
in general seem endless. In order to constrain the topic for this
column, we will investigate information technology based intelligence systems
that are evolving as we speak.The Global Intelligence Grid (GIG) is this
next generation of intelligence gathering systems that will serve to protect
against terrorism. In our technology analysis framework presented
in the first column, the GIG would be classified as a Defensive Tool for
Protection and without question the exact operations and capabilities would
fall under Black (Covert) Operations.
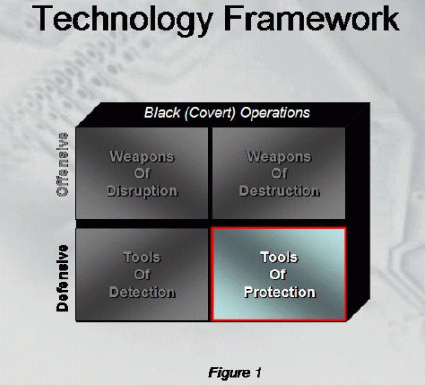 NOTE: Information Technology in general can and does play a much
broader role. IT applications can involve tools of detection and
weapons of mass disruption.
NOTE: Information Technology in general can and does play a much
broader role. IT applications can involve tools of detection and
weapons of mass disruption.
The Global Intelligence Grid will be the most complex systems development effort ever undertaken. While we can only speculate about the true capabilities, the following description should provide a glimpse into what the system might be like. To help define the GIG we can break it down into simple input systems, processing systems, and output systems.
A multi-layered approach would be used to create a sensor network array that collects data in real time and communicates that data back to the processing system. Advances in sensor technology has created the ability to decrease the size of these devices and with breakthroughs in semiconductor technology, decrease the power consumption; thus, extending the length of operational time and increasing communications power. This new breed of sensor will be much more intelligent. In essence they would hibernate until something happens that would cause the sensor to become stimulated. At which point the individual sensor or sensors would collect the specific type of information and send it back for processing and analysis. These sensors would also identify the presence of detection equipment and remain silent until it was safe to transmit the collected data.
The new sensors will be able to detect vibration, chemicals, radiation,
biological agents, explosives, footsteps, voices, still images, and even
video images and transmit them to a network of fixed and mobile relay collection
stations. The significant reduction in size will enable sensors
to be deeply embedded in the physical world products or materials and spread
throughout our environment like smart grains of sand.Currently, the sensor
networks with communications capabilities have been produces that are as
small as a penny. In the future NanoTechnology (the capability of
building things one molecule at a time) will create miniature sensors so
small they could be woven directly into the fabric of a chair or in the
layers of plastic in a milk carton or maybe even within the ink on a piece
of paper.
The multiple layers of networked sensors would consist of seven layers.
- Spaced Based Satellite Systems
- Airborne Based Combination Relay/Sensing Systems
- Elevated Land Based Sensors and Relay Systems
- Common Product Based Sensing Systems
- Ground based Sensors
- Sea Surface Sensing Systems
- Ocean Floor Sensor Systems
Collecting the information from the sensors is one thing, but making
sense out of all this data is another. Data collected and processed
becomes information - information analyzed, understood and put in context
is Knowledge. The GIG must not just collect this mountain of data
but also have the ability to transform the bits and bytes into information
and knowledge that can be acted upon. The ability to store the information
and extract meaningful information is another. Because of the unique
characteristics of the terrorist networks, careful attention must be given
to the location of each and every event, action, or fragment of information.
The ability to covertly sense and monitor events and activities on this
scale will stretch the limits our current Geographic Information Systems
(GIS) capabilities. GIS is a system of hardware and software used
for storage, retrieval, mapping, and analysis of geographic data in this
case sensory data.Spatial features are stored in a coordinate system latitude/longitude,
state plane, UTM, etc., which references a particular place on the earth.
Once the data is stored in the GIS system, advanced processing capabilities
such as data fusion must be employed to make sense out of events that may
be taking place in different parts of the world. Simply put: data
fusion is the seamless integration of data from disparate sources.It is
like picking a puzzle part out of a box containing pieces from 60 different
puzzles and selecting not only the puzzle it belong to but also where it
fits. These individual events may be meaningless, but put together
like pieces of a puzzle could indicate a terrorist attack. Advanced
pattern recognition techniques coupled with the GIS capabilities create
a powerful tool to combat terrorism and defend our homeland. GIS
with advanced drill down capabilities and interoperability with other pattern
identification tools must be an integral part of the GIG processing system.
Another information tool looks at not only the location of events, actions,
or information; but also who is involved must also be included in the processing
capabilities With complex relationships and the magnitude of information,
information overload must be overcome through the use of advanced visualization
techniques and automated profiling and modeling capabilities.One such
technique is advanced relationship mapping capabilities that identifies
known and in some cases obscure relationships between people or organizations,
calculates the weight of each relationship or connection based on actions,
events and intelligence and displays these relationship graphically in
a nodal relationship matrix. This allows rapid identification of
significant participants (leaders) within organizations and possibly the
network within or external to a terrorist cell.
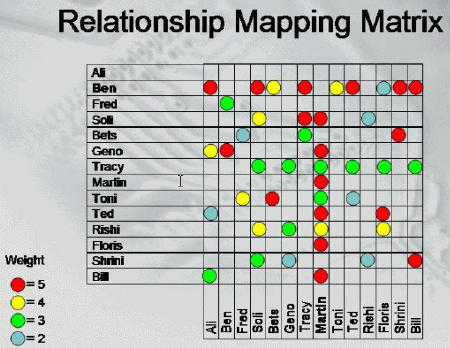
Figure 2
Data visualization is essentially a mapping process from computer representations to perceptual representations, choosing encoding techniques to maximize human understanding and communication.The goal of a viewer might be a deeper understanding of physical phenomena or mathematical concepts, but it also might be a visual proof of computer representations derived from the initial stage of intelligence analysis routines. Without the ability to quickly make sense out of the mountains of data the GIG will produce, we will not be able to interpret the sensory input data quick enough to intercede in clandestine activities. The work product of the automated analysis tools is every bit as important as the ability to collect the data to begin with.
BioTechnology and Homeland Security
BioTechnology is a strategic asset in the fight to protect the world's
population against bioterrorism.Laboratories in companies around the world
are actively developing biological detection and defense technologies.
While the BioTech industry in general has a long standing policy against
using this science to develop weapons, there are also labs working on creating
bioweapons.
Nearly 20 countries around the world possess biological weapons of mass destruction. It is important to note that BioTech used as a weapon not only target humans, but crops and livestock as well. There are four primary Biological agents used as weapons.
- Anthrax
- Botulism
- Plague
- Smallpox
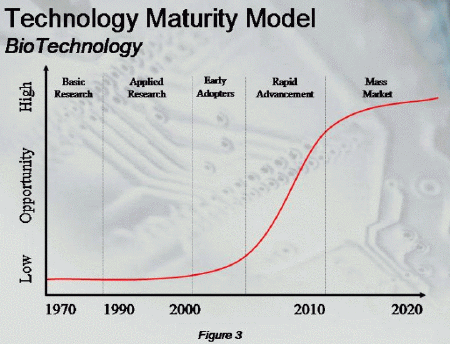
As a technology, BioTech is relatively immature.As BioTechechnology
advances, we can expect new applications of this science to create weapons
of mass destruction. As you can see by Figure 3, BioTechnology
is in the latter stages of the applied research phase of maturity.
 On the defense side of BioTechnology, companies are actively developing
biological defense technologies. Many of these initiatives are dual
purpose efforts, meaning they can be used for conventional health care
and biological defense.Other companies are in the early stages of developing
a number of products and platforms, including vaccines, therapeutics and
diagnostics, that can be enlisted to fight bioterrorism. As with
most technological advances, BioTech applications are moving from the research
labs into real world application in both the offensive (weapons of mass
destruction) and defensive categories and fall into both the white operations
and black (covert) operations.
On the defense side of BioTechnology, companies are actively developing
biological defense technologies. Many of these initiatives are dual
purpose efforts, meaning they can be used for conventional health care
and biological defense.Other companies are in the early stages of developing
a number of products and platforms, including vaccines, therapeutics and
diagnostics, that can be enlisted to fight bioterrorism. As with
most technological advances, BioTech applications are moving from the research
labs into real world application in both the offensive (weapons of mass
destruction) and defensive categories and fall into both the white operations
and black (covert) operations.
While there is very little direct impact technology can have on the
proliferation of biological weapons, it will play a pivotal role in alerting
the public of threats and releases of biological weapons. Currently,
air monitoring station within major metropolitan areas (areas of high threat)
have and are being retrofitted to include sensors to detect the presence
of biological agents. While not yet a real time system (as described
earlier) these detection systems are perhaps the first line of bioterrorism
detection. Our second line of defense rest with the network of health
care providers. As unknowing victims of a bioterrorism attack fall
ill they will seek diagnosis and treatment, health care providers must
recognize the symptoms and report it to our CDC that tracks such health
threats. Public health and homeland security officials recognize
that there's a very limited period of time to determine if an act of bioterrorism
has occurred and identify the organism before the disease spreads and creates
a second wave of exposed victims.
Once again this system uses GIS technology to monitor and track the spread the disease which will aid in limiting exposures and assist in tracing the initial point of release. The looming threat of bioterrorism has raised the level of angst and heightened the sense of urgency to enhance the existing systems that are used to monitor infectious diseases. A fully integrated, real time GIS would provide greater meaning to the data and speed the detection of disease outbreaks. In order to be effective the systems must address the multiple layers of care providers and agencies. One critical issue is the numerous points of data collection and the education of health care workers and first responders for early identification of victims.
Technology can not totally protect us against the threats of terrorism.
But it can increase our ability to prevent such acts or limit the impact
of the acts. As you can see technology is a double edge sword.
Just as nuclear technology can by used to treat cancer and provide electricity
- it can also be used in weapons. It is not the technology that we
should be concerned about, it is the application of the technology.
For decades governments have tried to control the spread of technology.
This has had only limited success. In a recent presentation a discussion
arose that suggests the only way to control technology is to control the
knowledge that is required to create it. What a scary thought!
There are already signs that this is occurring. Discussions are underway
that would limit the publication of general academic research in a number
of different areas. This is an effort meant to prevent the knowledge
transfer to undesirables. While one can certainly understand the
rational behind such actions, you have to consider just how much impact
this could have on the advancement of science and technology that would
serve to benefit all of mankind. Reducing collaboration and peer
review will greatly slow the advancement of scientific research.A delicate
balance must be struck as not to impair the evolution of science and technology.