From the corporate wars fought in
the boardroom to the war on terrorism fought in virtually every corner
of the world, technology provides combatants the ability to both protect
and destroy. This double- edged sword is the focus for this column
as the relationship between homeland security and technology will be explored.
While preparing for this column, it became necessary to construct a framework
to understand and to evaluate the role technology will play in homeland
security.
Our attention of late has been focused on WMD or weapons of mass destruction. However, there is a secondary meaning to WMD nearly as critical. It is weapons of mass disruption. Cyber Terrorism and the threat against a nation's infrastructure must also be considered in planning for homeland security.Statistically speaking, most terrorists still prefer guns, bombs, and other conventional weapons. However, evidence suggests that many of the "new" terrorist groups are willing to use unconventional weapons and methods to inflict mass casualties. Terrorist groups are becoming increasingly familiar with technology and its application as a weapon. This column will examine technology and the role it plays in homeland defense and security. The remainder of this column will be devoted to explaining the framework as a context to understand the scientific and technological implications.
Technology Analysis Framework
It is difficult to cover all aspects
of how technology can be used both offensively and defensively in the context
of homeland security. A framework has been constructed to assist
in the analysis of the implications that technology will have on homeland
security and defense.The framework is a four by four matrix (figure 1)
that is used to classify the technology applications. The following
explains the context of each axis and category.
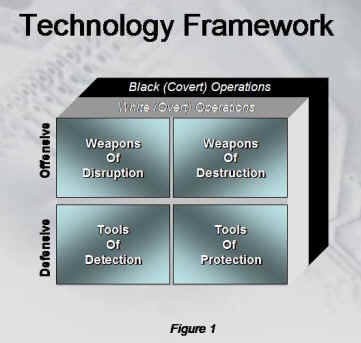
Application Axis
Offensive ApplicationsAs you can see, defensive applications rely heavily on information technology, intelligence, and knowledge acquisition. It is also important to know defensive tools can be policies enacted by governments to inhibit an enemies' ability to operate or acquire weapons and other resources necessary to launch an attack.
An "Offensive Application" includes any resource or technology that is used to destroy resources of the enemy. Typical examples that come to mind are bombs, missiles, and tanks, etc...Defensive Application
A "Defensive Application" includes any resources used to reduce the risk of destructive capabilities of an enemy. Typical examples would include radar, sensors (biological, nuclear or chemical), intelligence gathering networks, and so on.
Operations Axis White Operations
A "White Operation" is defined as any deployment of technology or resources that are visible or disclosed to the general public.
Example: The recent announcement that the Government would be upgrading the EPA Air Monitoring Stations in major cities to detect the presence of biological or chemical agents.
Black Operations
A "Black Operation" is defined as technology or resources that are NOT visible or disclosed to the general public.Example: (Just a concept) The United States intelligence communities create and deploy internet listening devices on the computers of known or suspected militant groups thought to be sympathetic to Al Queda.
Note: Our analysis of technology applications used in black operations in future columns will be purely speculative.Clearly, you can see that the black operations require secrecy or it would defeat the intention of the action. These covert activities gather information by many different means. It has long been known that a massive computing farm exists within the confines of the National Security Agency (NSA). In the government's fight to defend and protect all of us from terrorists, information from human sources, ground- based sensors, airborne intelligence platforms and satellites will be combined to monitor activities of known or suspected terrorists as well as to collect intelligence from which we can infer the plans of terrorists. The new war is all about information -- vast amounts of information from all over the globe.
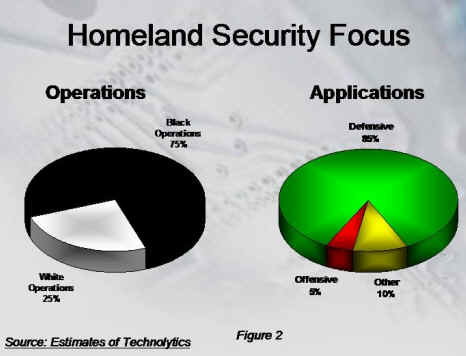
The focus of homeland security is
to protect the people of the United States against terrorist attacks.
Clearly the use of force or offensive weapons fall to the military and
some law enforcement agencies. As figure 2 suggests, the primary
tactics for securing the homeland will fall under "Black Operations."
We will never fully know the majority of the protections and activities
undertaken in an effort to ensure our security. While some find comfort
in that fact, others have expressed outrage over the possible loss of civil
liberties and privacy. In fact in the confirmation of Tom Ridge,
the first Secretary of Homeland Security, he was called upon to protect
the United States without dissuading individual's rights - a near impossible
task given the need to gather significant amounts of information on a broad
spectrum of topics.
Application Axis
The application axis addresses the way in which the technology will be used. The two different types of applications are offensive and defensive.
Offensive: Technologies that destroy the capabilities or resources of terrorists.
Weapons of DestructionDefensive: Technologies to safeguard or protect against terrorism.
A "Weapon of Destruction" includes chemical warfare agents, biological warfare agents, nuclear agents, and radiological agents, with the intentional release of industrial agents as a weapon or any destructive device or explosive.Weapons of Disruption
A "Weapon of Disruption" includes any intentional process, technique, or act used to upset the normal operation of society, government, or a nation's infrastructure.
Tools of DetectionOne element likely to change in the future is the availability of advanced weapons. Advanced weapons including weapons of destruction and weapons of disruption will proliferate. This growth will undoubtedly occur because technology is becoming cheaper and communications are making information including that of weapons more available, thus increasing the number of countries who have or will obtain advanced weapons. It will be harder to prevent small third world or under- developed countries from obtaining these weapons as well. Most recently, the government has openly expressed a deep concern over the open sharing of information by the research community. Up until now, scientific and technological research has been openly shared to foster collaboration among the research community. While the benefits of peer review, verification and collaboration are significant, so is the possibility that this information may be used by terrorists to "weaponize" biological agents making them resistant to current treatments.
A "Tool of Detection" includes intelligence-gathering systems, sensors to uncover the activities of terrorist and/or the presence of radioactive, biological, or chemical agents. These can include land- based sensors, air- based sensors, sea- based sensors and even spaced -based sensors.Tools of Protection
A "Tool of Protection" includes vaccines, intelligence, protective clothing, blast absorbing materials, neutralizing agents, and decontamination materials. It may also include new construction techniques and materials.
Example: Information from genetic research could be used to design biological weapons against specific ethnic or racial groups.(Currently, the production of such a weapon is only theoretical or at least it is believed to be.)
While no action has been taken to limit the access or distribution of research data in the post 9/11 era, one would expect it is only a matter of time.
It is clear that terrorists have
begun to use modern tools and technology to perform common terrorist activities.
We know they are interested in obtaining weapons of mass destruction and
evidence suggest weapons of mass disruption (cyber attacks) pose a significant
danger to a society addicted to information.
Advanced technologies are the key
to homeland defense and security. As research and development of
new and improved technological components are integrated together to provide
multiple layers of security one must consider the social, business and
legal implications. Technologies such as smart I.D.cards, face recognition,
smart documents (visas and passports), digital surveillance, and data fusion
techniques are just a sample of the tools we can use to combat terrorism
both at home and abroad.
With the framework described above, we will investigate the application of four specific areas of emerging technology on homeland security and defense.
- April - Information Technology and BioTerrorism
- June - NanoTechnology and the Fight Against Terrorism
- August - Data Fusion - Detecting Outbreaks after an Attack
- October - Cyber Terrorism - Can we secure the Internet?
- December - Communication Technology for Homeland Security
- Enhancement of bacterial & viral virulence
- Gene expression & protein engineering of toxins
- Genetic Weapons
One thing is clear. The value of information technology in the war against terrorism is ever increasing. Information technology can be used as an offensive or defensive tool/weapon. Offensive use of information technology may include systems or software that deny, exploit, corrupt, or destroy an adversary's information, information-based processes, information systems, and computer-based networks while protecting one's own. Defensive use of information technology may include intelligence gathering systems, sensor networks, alerting and communications systems, and systems that interrupt massive amounts of data to uncover patterns of activities related to terrorism. It seems very clear that the above introduction to technology and homeland security suggests that technology provides both the tools for terrorists and the defenses to combat terrorism.