Communications Intelligence
Communications Intelligence really began in 1924 when the Navy established
a Communication Intelligence Organization under the Code and Signal Section
of the Office of Naval Communications. The phrase "communications
intelligence" (COMINT) means intelligence produced by the study of foreign
communications, including the breaking, reading, and evaluating enciphered
communications.This excludes public information such as news papers, television
news reports and other broadcast forms of public communications.
Cryptography is a term which is applied to cipher activities, the construction
of ciphers and the breaking of ciphers. Since then the science of
communications intelligence has advanced along with the addiction of business,
government and the military on information.
Perhaps the best example of just how far communications intelligence
has advanced is ECHELON.While ECHELON has been in existence for about
20 years, only recently (1998) has it come into public view.
Echelon is without question the most powerful intelligence gathering capability
in the world. According to these reports, ECHELON captures volumes
of satellite, microwave, cellular and fiber-optic traffic, including communications
to and from North America.ECHELON is a global network of receivers and
computers that automatically searches through millions of intercepted messages
for pre-programmed keywords.Every word of every message in the frequencies
and channels selected at a station is automatically analyzed. Advances
in speech recognition have increased the capacity to efficiently and effectively
extract intelligence from voice data. When this vast quantity of
communications is then processed through sophisticated technologies and
intelligence is derived. (See Figure 1 Communications Intelligence
Process Diagram) Integrated with GIS mapping capabilities and voice recognition
software you know who said what, where and when.
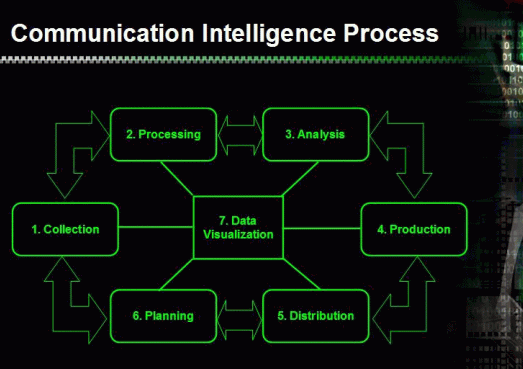
Figure 1
Component #1 Collectors - This component intercepts the raw data. Satellites, massive microwave receivers, and wide spectrum radio receivers are all used to acquire access to communications. Since the actual number of these collection components is a secret, experts estimate that there are about 150 satellites used in this operation. The biggest challenge is optical networks. These optical communications systems in many cases require expensive and risky intrusive techniques to covertly intercept information.
Another challenge is the volume of data now being transmitted with millions upon millions of messages being intercepted each and every day. A relatively new challenge has emerged and that is cloaking and encryption techniques that mask the information.
Component #2 Processors - Millions of intercepts are developed every hour. From this massive "stack of hay" the computers must identify the small number of needles that exist. The millions of hourly intercepts are filtered down to perhaps a few thousand. These intercepts are then forwarded for detailed analysis and human intervention. A massive amount of processing capacity is needed to handle the volumes of raw data and the significant array of pattern templates that are used to detect possible Intercepts of Interest (IOI). The most advanced facilities leverage Grid Computing to meet this challenge. Grid applications couple resources that cannot be replicated at a single site or may be globally distributed for other practical reasons. Grid Computing Applications lets the intelligence community solve larger or new problems by pooling together multiple computers.
Component #3 Analyzers - The Analyst Workstation (Figure 2) and associated applications make up this component. Advanced algorithms and data fusion techniques are used to assimilate disparate pieces of information from multiple sources to create multiple views of the data. The analyst's workstation provides the capability to effectively analyze and appropriately utilize information from classified sources along with open sources such as news feeds, web spiders, software agents, and public records in the global climate. These multiple view and data sources allow analysts to discern patterns and relationships that may otherwise escape detection. After processing the analyst reduce the number of intercepts down to only the ones with the highest probability and credibility scores.
Component #4 Production - Only about 20 intercepts with detailed follow on analysis meet the criteria to be included in an analysts report. The analyst report depicts the current condition, trends, predictive events, and strategic moves that are all related to a single event scenario. Each scenario is ranked as to the degree of confidence in each piece of data making up the scenario as well as the probability of the event making it through to realization in the short-term, near-term, or even long-term. A recommended distribution list is generated by the system based on the circumstances of each scenario.
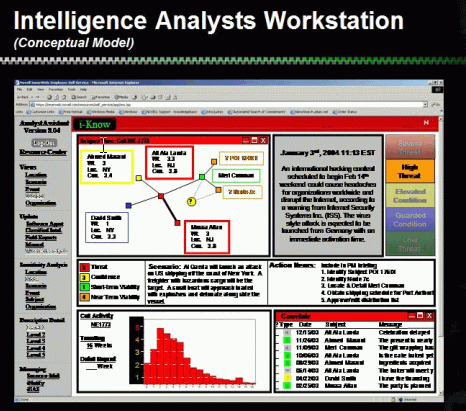
Figure 2
Component #5 Distributors - Once the distribution list is approved, the electronic document is encrypted and electronically delivered to those individuals and agencies identified by the system or added manually by the analyst or management. Once the recipient is authenticated and opens the electronic document, a receipt message is returned to the initiating system and the completed transaction is logged. The multi-stage secret key to decrypt the message at the recipient's workstation enables the message to be read.
Component #6 Planning - This component determines what information is required and what are the potential sources from which the intelligence can be obtained. Once the resources are identified, they are scheduled and all necessary preparations are made. This directs specific intercept activities and manages the vast amount of general intercepts that routinely take place each and every minute.
Component #7 Visualization - This component creates a graphical representation of the scenario, event, data, or relationship matrix. Like good writing, data visualization techniques displays or communicate information with clarity, precision, and efficiency. This component creates highly interactive 2D and 3D graphics that can be viewed in multiple ways that are fully selectable by the user. Included in the suite of capabilities are drill-down capabilities that allow the user to click on an object and track completely back to all the intercepts and data that are related to the event or scenario.
While these seven components make up a significant portion of the overall system, several other subsystems are worth mentioning.
Subsystems Include:
- Secure role-based identity management
- Pattern based learning
- Encrypted communication and messaging
- Hypotheses generator
- Remote job submission and management
- Remote Intelligent Agent Monitors (software agents not people)
- Probability analysis
- Recursive analysis
- Remote file transfer and archiving
- Composition of Grid resources
- Job, system and resource scheduling
- Distributed Data Visualizations
- Dissemination of jobs dynamically based on identity and roles
- Dynamic configuration of the Grid (Nodes can join or leave the grid at any time)
All the intelligence we have discussed thus far is targeted for use by the intelligence community. But what about civilians? If a terrorist threat were to be uncovered, other than the Color Coded Systems created by the Department of Homeland Security - how would the public be notified of specific threats and measures that should be taken. A civilian distribution capability is necessary.
Civilian Distribution Capability
Communications is by far the most critical component of the Homeland Security infrastructure. Without it all the intelligence, planning and preparations are without value. Concerns surrounding public safety have been heightened due to inadequate communication or often times inaccurate information. With the magnitude of media coverage, in the absence of facts, assertion or inaccurate information fills the void. Virtually every study of disasters, including September 11th terror attacks identify communications as an area that significantly need improvement.
The Emergency Broadcast System (EBS) was initiated in 1963 during the Kennedy Administration to allow the President to address the entire nation in an emergency.Later the EBS was further expanded through an inter-agency effort with the FCC, FEMA, and the National Weather Service (NWS) to permit the system to be used for state and local emergencies.Under the EBS program, equipment that allowed the President to reach the public through their local broadcasters was required at broadcast stations licensed by the FCC.
Did the Emergency Broadcast System go off on September 11th? NO
Times have changed and now many people get their news and information via the Internet. Satellite radio and cable television have also served to decrease the effectiveness of the current EBS. In addition, millions of employees work in areas where radios and televisions are absent - thus being out of touch with the EBS and alerts, which could save their lives. The time has come to bring the EBS into the information age and the way to do this is by the development of a new fully integrated system. The system must incorporate all aspects of 21st century communications. Delivery of the alert must accommodate: cell phones, pagers, BlackBerry devices, set-top boxes (TVs), electronic dashboards (like OnStar), satellite radio, as well as traditional radio and TV broadcasting. The solution must provide a single, inter-agency alerting system and communications process to alert citizens in times of emergency or terrorist attack.It must be able to target specific geographic areas and provide the mechanism to deliver more detailed instructions on what to do. (Figure 3)
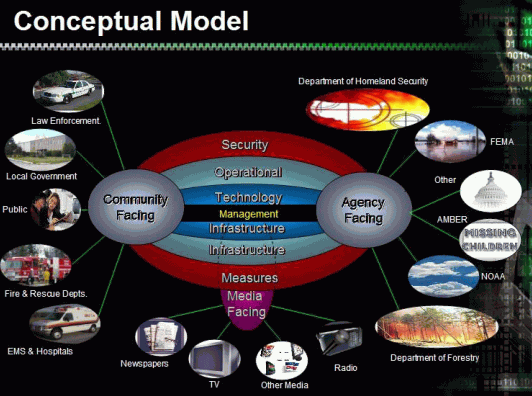
Figure 3
This alerting platform could even be applied to the AMBER alerting system on a national basis. The geographic targeting function would allow specific areas of interest to receive the information while eliminating alert overload from too many messages. The government has done much too little to prepare the general population for the next terrorist act that looms just over the horizon. While it is clear prevention must be the primary focus for DHS and our leaders; however, if a terrorist launched a chemical or biological attack on U.S.soil, quick, accurate and targeted information could reduce the loss of life, exposures, and the cost of treatment to civilians and first responders.